Blog

Coronavirus cyber-attacks update: beware of the phish
- New phishing campaigns discovered impersonating the WHO and popular conferencing platforms, to steal sensitive information
- Check Point has seen 192,000 coronavirus-related cyber-attacks per week over the past three weeks, a 30% increase compared to previous weeks
- In the past three weeks, almost 20,000 new coronavirus-related domains were registered: 17% of these are malicious or suspicious
While we all try to get used to the Covid-19 pandemic’s ‘new normal’ in our work and home lives, this year has been a time of unprecedented opportunity for cyber-criminals. The global response to the pandemic, and our desire for the latest information about it, has supercharged criminals’ and hackers’ business-as-usual models of phishing emails and fake websites.
Both Interpol and Europol have warned of huge spikes in COVID-19 fraud. In mid-April, Google reported that in just one week, it saw more than 18 million daily malware and phishing emails related to Covid-19 scams were sent via Gmail alone – and that’s in addition to the 240 million daily Covid-19 related spam messages Google saw.
So why do criminals rely so heavily on phishing emails to launch attacks? The answer is simple: because they continue to work. Verizon’s 2019 Data Breach Investigations Report showed that 32% of corporate data breaches started with a phishing email. What’s more, phishing was present in 78% of cyber-espionage incidents. So it’s no surprise that criminals will keep on trying to trick users into giving up sensitive information by taking advantage of the interest around the pandemic, and impersonating well-known organizations and companies such as the World Health Organization (WHO), Zoom, Microsoft or Google.
WHO is phishing me?
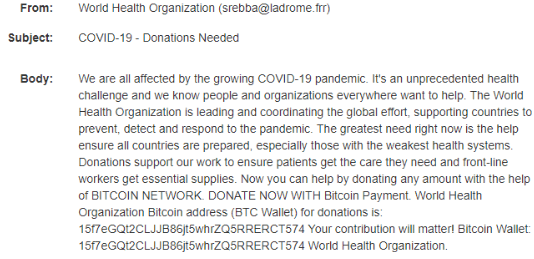
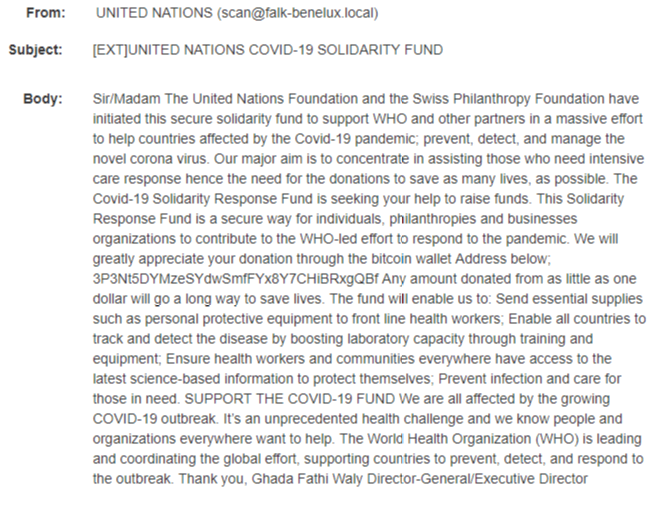
For example, cyber criminals have recently sent malicious emails posing as the WHO from the domain “who.int” with the email subject, “Urgent letter from WHO: First human COVID-19 vaccine test/result update” to lure victims. The emails contained a file named “xerox_scan_covid-19_urgent information letter.xlxs.exe “ that contained the AgentTesla malware. Victims who clicked on the file ended up downloading the malware.
We also found two examples of extortion emails supposedly sent by the United Nations and WHO asking for funds to be sent to several known compromised bitcoin wallets, as seen below:
Impersonating video conferencing apps
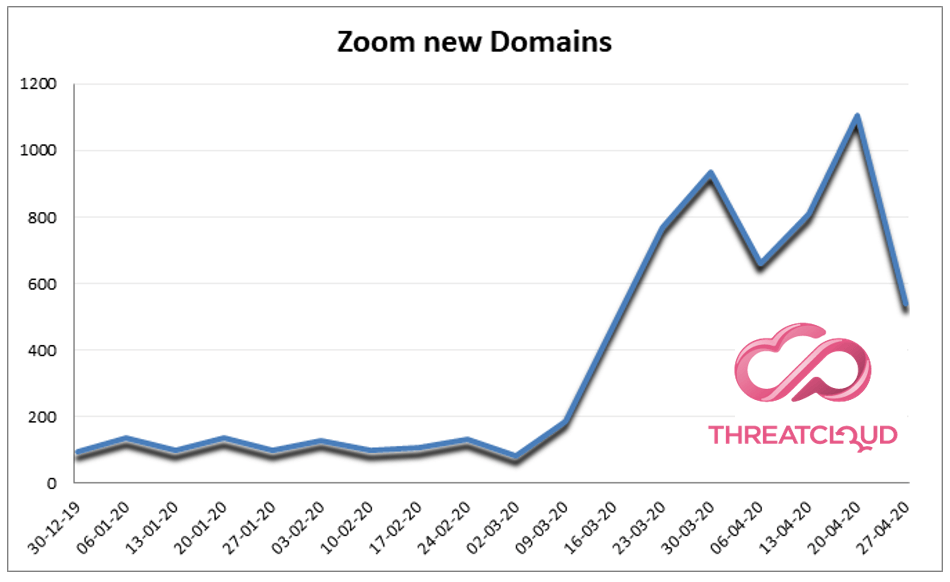
As working from home is now the norm for a majority of people during the pandemic, we have reported previously how cyber criminals were using fake Zoom domains for their phishing activity. In fact, in the last 3 weeks alone, around 2,500 new Zoom-related domains were registered (2,449). 1.5% of these domains are malicious (32) and other 13% are suspicious (320). Since January 2020 to date, a total of 6,576 Zoom-related domains have been registered globally.
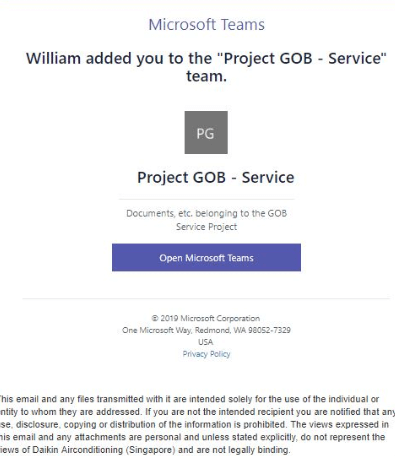
And Zoom isn’t the only platform cyber criminals are impersonating – both Microsoft Teams and Google Meet have been used to lure victims too. Recently, victims fell prey to phishing emails that came with the subject “You have been added to a team in Microsoft Teams“. The emails contained a malicious URL ”http://login\.microsoftonline.com-common-oauth2-eezylnrb\.medyacam\.com/common/oauth2/” and victims ended up downloading malware when clicking on the “Open Microsoft Teams” icon that led to this URL. The actual link for Microsoft Teams is “https://teams.microsoft.com/l/team”.
Then there are fake Google Meets domains like Googelmeets\.com, which was first registered on April 27, 2020. Of course, the link did not lead victims to an actual Google website.
Coronavirus related cyber-attacks increase
Over the past three weeks there has been 192,000 coronavirus-related attacks per week, a 30% increase when compared to the previous weeks. We define coronavirus-related attacks as those that involve
- Websites with “corona”/”covid” in its domain
- Files with “Corona” related file names
- Files that have been distributed with coronavirus-related subjects in their email
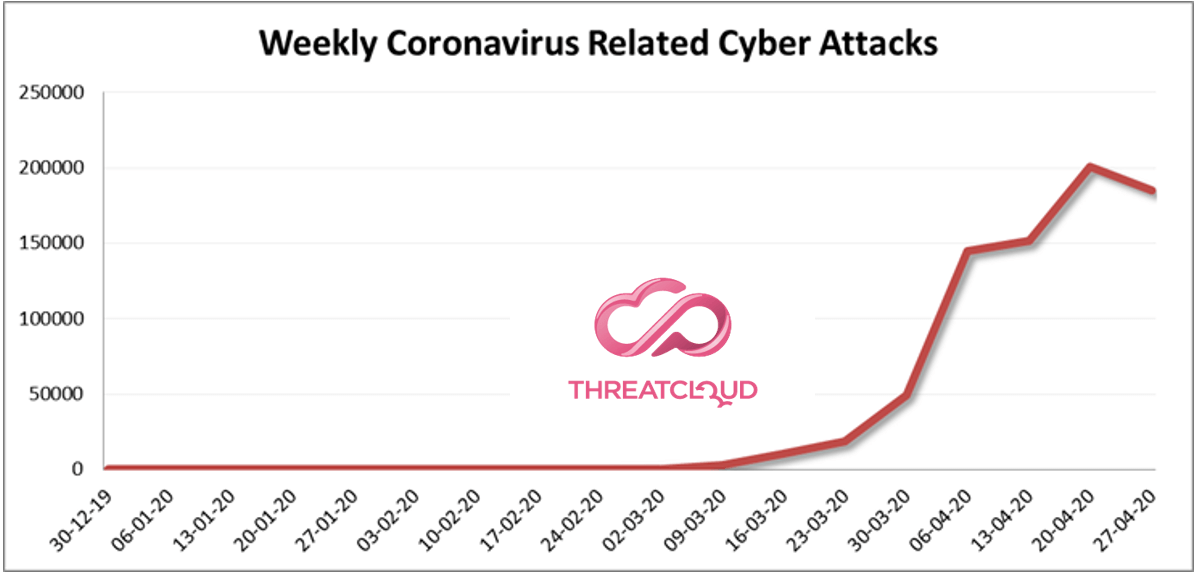
The graph represents all coronavirus-related attacks, detected by Check Point’s Threat Prevention technologies across networks, endpoints and mobile devices, stored and analyzed in ThreatCloud, the world’s most powerful threat intelligence database.
Coronavirus-related domains
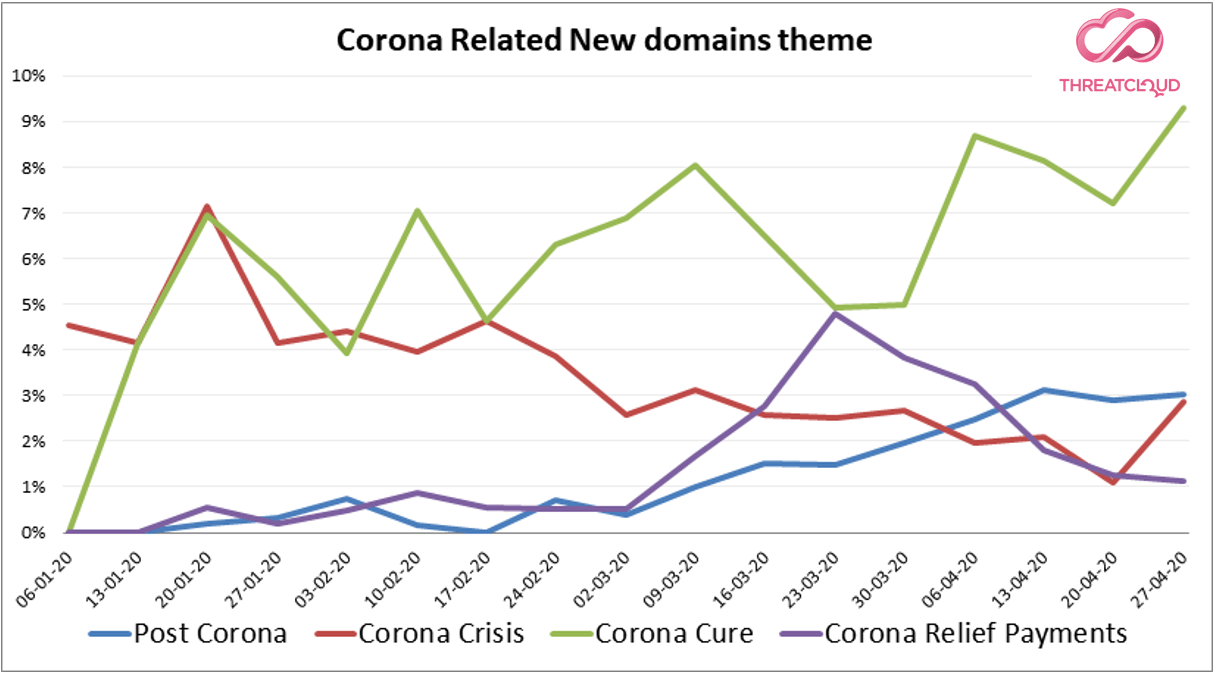
When looking at new coronavirus-related registered domains, we have observed that the domains were representing different stages of the pandemic outbreak around the world.
- At the beginning of the outbreak, domains related to live maps (tracking geographic areas that saw a rise in coronavirus cases) were very common, as well as domains related to coronavirus symptoms.
- Towards the end of March, the focus turned to relief packages and stimulus payments due to the economic plans executed by several countries.
- Since several countries have started easing restrictions, and begun planning the return to normal life, domains related to life after the coronavirus have become more common, as well as domains about a possible second wave of the virus.
- Along the entire pandemic timeframe, domains related to tests kits and vaccines remain very common, with slight increases as time goes on.
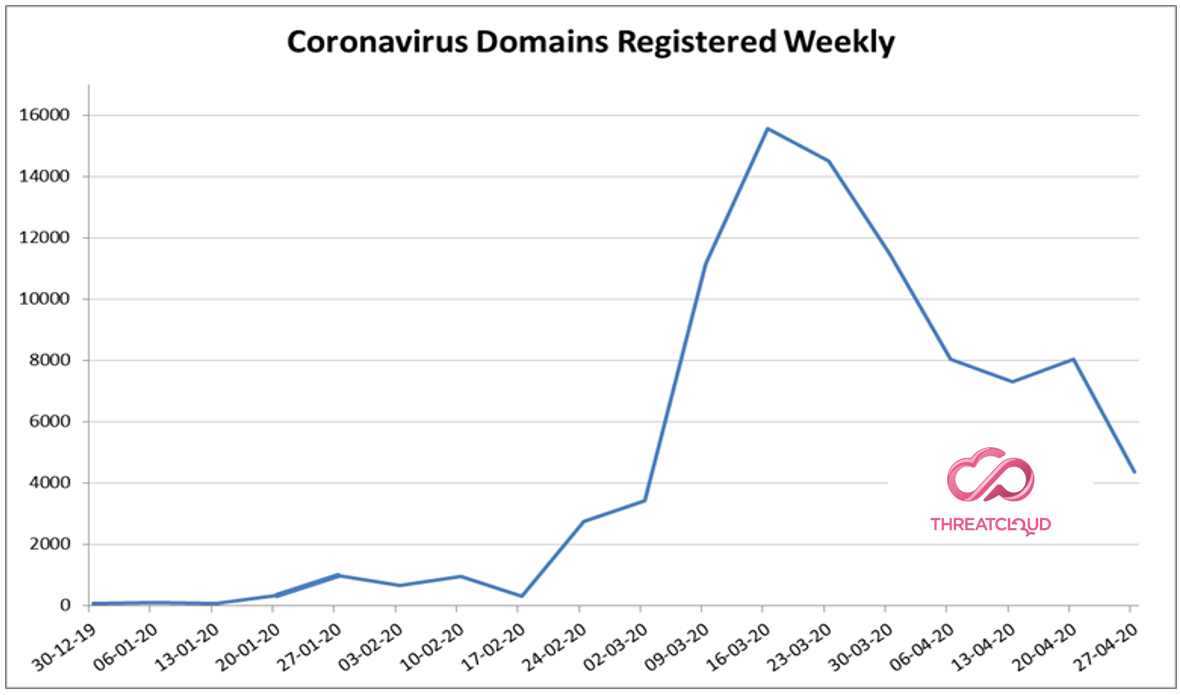
As we previously reported, since mid-February we have seen an escalation in the number of coronavirus-related domains being registered. In the past three weeks almost 20,000 (19,749) new coronavirus-related domains were registered. 2% of these domains are malicious (354) and another 15% are suspicious (2,961).
So far, since the beginning of the outbreak, a total of 90,284 new corona related domains have been registered globally.
Staying protected against Coronavirus-related phishing attacks
For a phishing attack to be successful, it has to trick users. So to protect yourself, be suspicious of any email or communication from a familiar brand or organization that asks you to click on a link or open an attached document, no matter how official it appears to be. A legitimate email should never ask you to take these actions. Here are five golden rules to help keep your data safe:
- Beware of lookalike domains, spelling errors in emails or websites, and unfamiliar email senders.
- Be cautious with files received via email from unknown senders, especially if they prompt for a certain action you would not usually do.
- Ensure you are ordering goods from an authentic source. One way to do this is to NOT click on promotional links in emails, and instead, Google your desired retailer and click the link from the Google results page.
- Beware of “special” offers. “An exclusive cure for coronavirus for $150” is usually not a reliable or trustworthy purchase opportunity. At this point of time there is no cure for the coronavirus and even if there was, it definitely would not be offered to you via an email.
- Make sure you do not reuse passwords between different applications and accounts.
Also, organizations should prevent zero-day attacks with an end to end cyber architecture, to block deceptive phishing sites and provide alerts on password reuse in real time. Check Point Infinity is effective because it combines two key ingredients: full convergence across all attack surfaces and all attack vectors, and advanced prevention that can tackle the most sophisticated zero-day phishing and account takeover attacks.
Fonte: https://blog.checkpoint.com/2020/05/12/coronavirus-cyber-attacks-update-beware-of-the-phish/